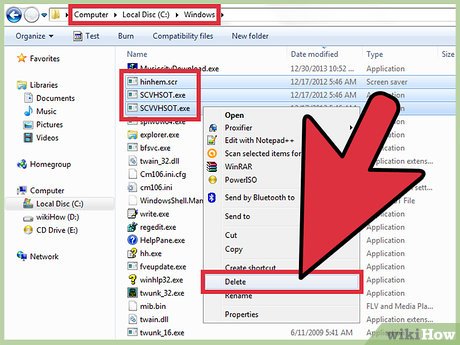
Now to actually delete the virus from the system go to system32 folder and delete the regsvr.exe virus file from there (you will need to uncheck the option of “Hide Protected System Files and Folders” in Folder Options to view the virus file).
How can I remove exe virus from my computer?
Now to actually delete the virus from the system go to system32 folder and delete the regsvr.exe virus file from there (you will need to uncheck the option of “Hide Protected System Files and Folders” in Folder Options to view the virus file).
Can you virus scan an exe?
These days all Windows versions come with Windows Security (formerly Microsoft Defender), and Windows Security has a built in easy way to scan specific .exe files. If the file is on your desktop right click it and choose “scan with Microsoft Defender”.
How do you check if .exe has malware?
Another way to find out if the EXE is legit is to scan it with VirusTotal. You simply upload the suspicious file on the VirusTotal website, and this online scanner will check it for all types of malware.
Can an exe infect without running?
So big yes, you can get viruses without executing exe files.
Can exe files be hacked?
One of the most common tricks used by hackers is to get unsuspecting users to click on a malicious .exe file which leads to malware being downloaded onto a computer. They’re usually sent to you as an email attachment with the email offering some form of compelling inducement to get you to open the attachment.
Can an exe run without clicking on it?
Yes, in the context of the browser, since unintentionally you’re executing the page without clicking on anything. Such viruses are capable of downloading themselves to your hard disk without your cooperation.
Is Windows Defender good enough?
Microsoft’s Defender is pretty good at detecting malware files, blocking exploits and network-based attacks, and flagging phishing sites. It even includes simple PC performance and health reports as well as parental controls with content filtering, usage limitations, and location tracking.
Is Sonic exe a virus?
Overview. Malware Sonic, or Mal, for short, is a computer virus that was made to look like a Sonic the hedgehog fan game to fool people into downloading it. The virus later became conscious and nowadays it just likes surfing the web trying to find computers to get inside of and control.
How do viruses get on your computer?
How a Computer Gets a Virus. There are several ways a computer can get infected by a virus and most of them involve downloading – either intentionally or unintentionally – infected files. Pirated music or movies, photos, free games and toolbars are common culprits, as are phishing/spammy emails with attachments.
How can I remove virus from my computer without antivirus?
The first step towards removing a virus is identifying and stopping it from further infecting your device. To do that, press Ctrl + Alt + Delete and open the task manager. Then, go to ‘Processes’ and check for any unfamiliar programs running. To confirm if it is a virus, search online.
How do I force a program to Uninstall?
Press down the CTRL+SHIFT+ESC keys together to open the Task Manager. It should already be on the processes tab. Select the Program or App you want to uninstall from the list under processes. Now try running the uninstall on the Program/App again.
How do I delete hidden Apps on Windows 10?
Press Win + R to open the Run command dialog box. Type appwiz. cpl and press Enter to open the Programs and Features window. Next, locate the app you want to remove, right-click on it, and select Uninstall.
Which virus attaches itself directly to an exe?
Direct Action Virus – When a virus attaches itself directly to a .exe or .com file and enters the device while its execution is called a Direct Action Virus. If it gets installed in the memory, it keeps itself hidden. It is also known as Non-Resident Virus.
Can you get a virus just from downloading a file?
Malware often will sneak onto a system through a legitimate download, and then infect your system. Think of it like the Trojan Horse of Greek mythology. In fact, that is where the classification of malware Trojan gets its name, by masquerading as a legitimate file, then infecting your system.
Can a virus work without opening it?
Viruses per se usually can’t be triggered or spread when they are not opened, as a virus needs to be executed to spread or do damage. See the answers below for some scary exceptions. However, there are other types of malware, like worms, that can.
What is DrvInst exe?
“DrvInst.exe” installs device driver software to create communication between a hardware device, (such as a disk drive, printer, speaker, or mouse), and the computer operating system or an application.
What language is .exe written in?
An EXE file is a type of program that runs in Microsoft Windows. It consists of binary, machine language code that’s not designed to be read or written by humans.
Does Windows Defender remove viruses in Windows 10?
The Windows Defender Offline scan will automatically detect and remove or quarantine malware.
What does Windows Defender do when it finds a Virus?
As soon as a malicious file or software is detected, Microsoft Defender blocks it and prevents it from running. And with cloud-delivered protection turned on, newly detected threats are added to the antivirus and antimalware engine so that your other devices and users are protected, as well.
How do I know if I have a Virus on Windows 10?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Do I need another antivirus if I have Windows Defender?
Windows Defender scans a user’s email, internet browser, cloud, and apps for the above cyberthreats. However, Windows Defender lacks endpoint protection and response, as well as automated investigation and remediation, so more antivirus software is necessary.