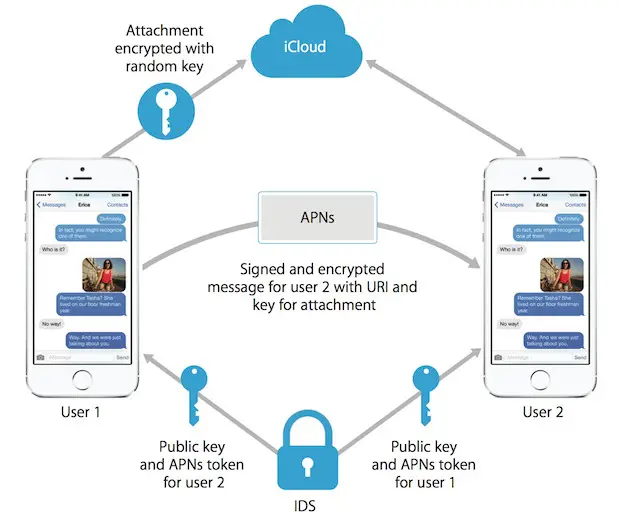
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.
Is iMessage really secure?
We designed iMessage to use end-to-end encryption, so there’s no way for Apple to decrypt the content of your conversations when they are in transit between devices. Attachments you send over iMessage (such as photos or videos) are encrypted so that no one but the sender and receiver(s) can access them.
Can iMessage be hacked?
Apple iMessage uses end-to-end encryption, and it is one of the safest messaging apps available right now. In addition, it uses a security system known as BlastDoor to protect it against malware attacks. It is a safe app because all the photos, videos, and other attachments have encryptions.
Can iMessage be tracked?
“IMessages between two Apple devices are considered encrypted communication and cannot be intercepted, regardless of the cell phone service provider,” the agency’s intelligence note.
Is iMessage really secure?
We designed iMessage to use end-to-end encryption, so there’s no way for Apple to decrypt the content of your conversations when they are in transit between devices. Attachments you send over iMessage (such as photos or videos) are encrypted so that no one but the sender and receiver(s) can access them.
Can iMessage be hacked?
Apple iMessage uses end-to-end encryption, and it is one of the safest messaging apps available right now. In addition, it uses a security system known as BlastDoor to protect it against malware attacks. It is a safe app because all the photos, videos, and other attachments have encryptions.
Can iPhone get hacked through iMessage?
Experts say that just receiving an iMessage from a hacker using this exploit can be enough to leave users’ personal data exposed. “It’s like being robbed by a ghost,” Hubbard wrote.
Can the police see your iMessages?
Law enforcement can retrieve messages via Google / iCloud backups. The chart shows that subpoenas will not grant access to message content for six of the nine secure messaging apps. The three that do give up “limited” content are iMessage, Line and WhatsApp.
Can iMessages have viruses?
But most iPhone users have nothing to worry about, according to Tomaschek. “The good news is that it is extremely uncommon for iPhones to get viruses due to the stringent security measures Apple builds into their devices, along with the App Store security requirements for app developers.
Can someone hack my phone by texting me?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
Can someone else read my iMessages?
They can only view this information if they are logged into your account on their iDevice. For example, an iPhone, iPad and MacBook all on the same account will receive all messages sent or received from the other machines (barring a lack of network connectivity). My suggestion to you is to change your password.
Can police recover deleted iMessage?
Keeping Your Data Secure So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
How long are iMessages saved?
For example, on an Apple device, you can choose to keep messages for 30 days, 1 year or forever.
Is iMessage safer than WhatsApp?
Because it uses end-to-end encryption, WhatsApp is inherently the safer option than other messaging apps. Yes, that includes Facebook Messenger, Instagram Messages, Snapchat, and even regular old iMessage. But it’s not 100 percent foolproof either…
Are iMessages safer than SMS?
As a result, iMessages are end-to-end encrypted. This means that, unlike SMS messaging, where your cellular provider can read your messages, Apple cannot. However, you must note that no messaging method is 100% secure as all systems are at-risk of hacking.
Who can see my iMessages?
1 Answer. Show activity on this post. They can only view this information if they are logged into your account on their iDevice. For example, an iPhone, iPad and MacBook all on the same account will receive all messages sent or received from the other machines (barring a lack of network connectivity).
Is iMessage safer than WhatsApp?
Because it uses end-to-end encryption, WhatsApp is inherently the safer option than other messaging apps. Yes, that includes Facebook Messenger, Instagram Messages, Snapchat, and even regular old iMessage. But it’s not 100 percent foolproof either…
Is iMessage really secure?
We designed iMessage to use end-to-end encryption, so there’s no way for Apple to decrypt the content of your conversations when they are in transit between devices. Attachments you send over iMessage (such as photos or videos) are encrypted so that no one but the sender and receiver(s) can access them.
Can iMessage be hacked?
Apple iMessage uses end-to-end encryption, and it is one of the safest messaging apps available right now. In addition, it uses a security system known as BlastDoor to protect it against malware attacks. It is a safe app because all the photos, videos, and other attachments have encryptions.
Can I tell if my iPhone has been hacked?
How can I tell if my iPhone has been hacked? The easiest way to tell if your iPhone has been hacked is by running a full device scan with top-tier antivirus security software. This will check your iPhone for any suspicious apps or activity and alert you to any unusual behaviors that may have gone unnoticed.
Can someone track my iPhone text messages?
If someone installs spyware onto your device, then they can remotely access any of the data on your iPhone – including all of your text messages.
Can FBI see your iMessage?
All but one (IP address) of iMessage can be accessed by the FBI. For WhatsApp, Line and iMessage, the access to message content is limited, while in the remaining, the FBI said it has no access to message content.