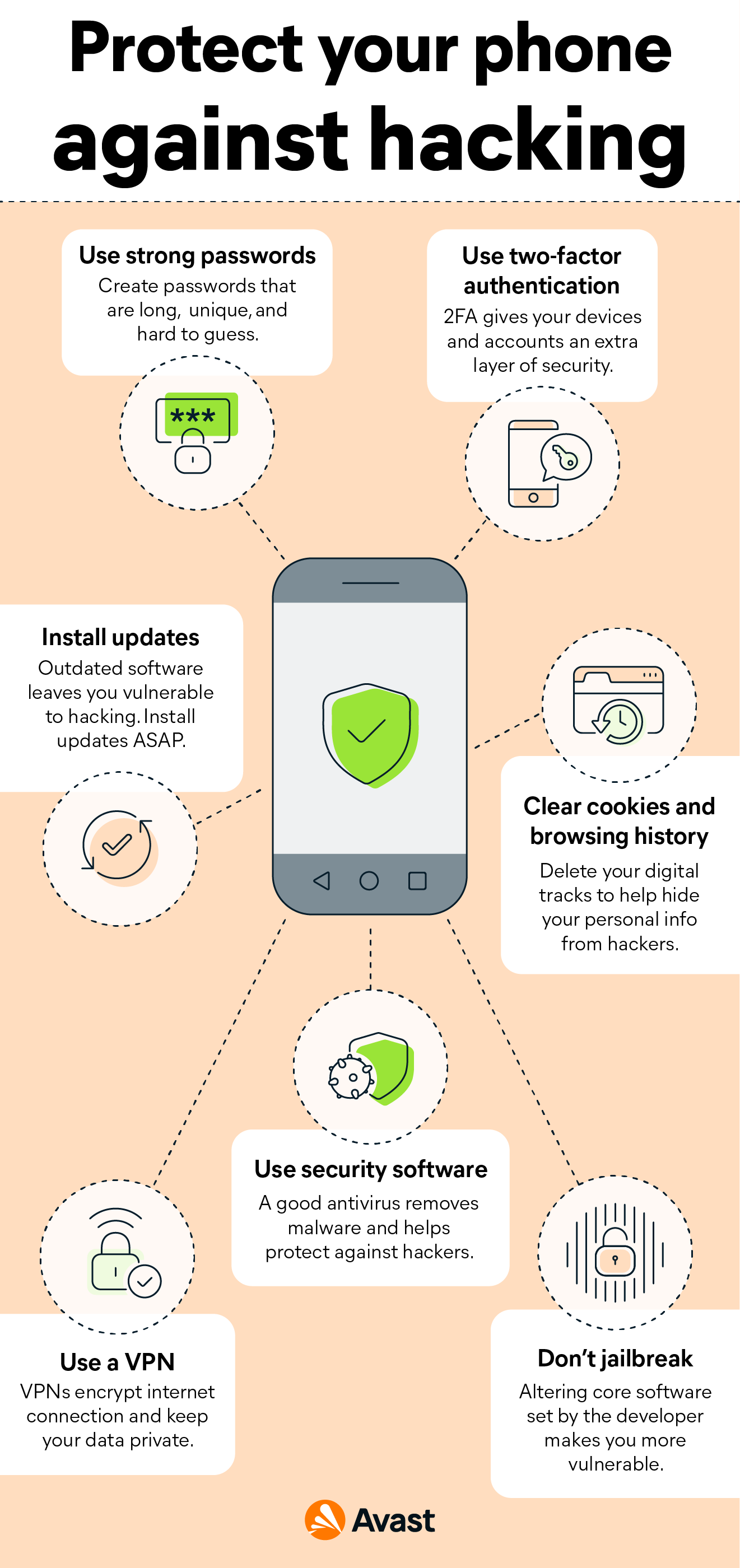
Hackers can use keyloggers and other tracking software to capture your phone’s keystrokes and record what you type, such as search entries, login credentials, passwords, credit card details, and other sensitive information.
Can hacker see you through your phone?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
What can be seen if phone is hacked?
“Therefore, if someone hacks your phone, they would have access to the following information: email addresses and phone numbers (from your contacts list), pictures, videos, documents, and text messages.” Additionally, he warns, hackers can monitor every keystroke you type on the phone’s keyboard.
Can someone hack my phone and see what I am doing?
It masks your IP address and encrypts your traffic, thus enhancing your privacy and security. Since hackers won’t be able to identify you online and monitor what you’re doing on your smartphone, they will have fewer ways to harm you. VPN is also useful if you use public Wi-Fis, which are not always safe.
What can be seen if phone is hacked?
“Therefore, if someone hacks your phone, they would have access to the following information: email addresses and phone numbers (from your contacts list), pictures, videos, documents, and text messages.” Additionally, he warns, hackers can monitor every keystroke you type on the phone’s keyboard.
Can you tell if your phone is being monitored?
Can you tell if your phone is being monitored? Yes, there are signs that will tell you when your phone is being monitored. These signs include overheating of your device, the battery draining fast, receiving odd text messages, hearing weird sounds during calls, and random reboots of your phone.
Can hackers see through your camera?
Are hackers really spying on people through their phone cameras and webcams? The short answer: Yes. Webcams and phone cameras can be hacked, giving bad actors complete control over how they function. As a result, hackers can use a device’s camera to both spy on individuals and search for personal information.
Can hackers access phone when off?
Answer: Unfortunately, yes. Turns out that shutting off a device still isn’t enough to stop the hackers anymore. A team of cybersecurity researchers at the Technical University of Darmstadt in Germany have discovered that iPhones can still be infected with malware when they’re powered down.
What can be seen if phone is hacked?
“Therefore, if someone hacks your phone, they would have access to the following information: email addresses and phone numbers (from your contacts list), pictures, videos, documents, and text messages.” Additionally, he warns, hackers can monitor every keystroke you type on the phone’s keyboard.
Can someone hack my phone and see what I am doing?
It masks your IP address and encrypts your traffic, thus enhancing your privacy and security. Since hackers won’t be able to identify you online and monitor what you’re doing on your smartphone, they will have fewer ways to harm you. VPN is also useful if you use public Wi-Fis, which are not always safe.
What do hackers usually look for?
For the majority, the incentive is simple and somewhat unsurprising: money. Most hackers will be focused on growing their personal wealth, that is why they will often resort to blackmailing their victims through ransomware or using various phishing techniques to trick them into making a bogus financial transfer.
What are hackers looking for?
The goal might be financial gain, disrupting a competitor or enemy, or theft of valuable data or intellectual property. Their clients might be nation-states, companies interested in corporate espionage, or other criminal groups looking to resell what the hackers steal.
What information do hackers look for?
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.
Can someone watch you through your phone camera?
Yes, you can be spied upon through the camera of your smartphone. There are several applications that can be found online that assist in spying on someone through their cell phone camera.
Can a hacker turn on your camera without you knowing?
But, just like any other tech devices, webcams are prone to hacking, which can lead to a serious, unprecedented privacy breach. Think of a case where an authorized person accesses and illegally takes control of your webcam, without your knowledge. Such a person will effortlessly spy on you and the people around you.
Can hackers see what websites you visit?
Hackers. A hacker can use attacks to see your browser history, login information, financial data, and more.
How do hackers track you?
Professional Ethical Hackers use email addresses as the primary link to identify, monitor, and track individuals on the Internet. Major email providers always provide you with options to disable and delete accounts, you just need to find the settings and security pages and start the process.
Can hackers hear your conversations?
It’s also a common misconception that a phone can be hacked or that someone can listen to your phone calls just by knowing your phone number. This is not possible and is completely false. You can read more information here.
Can hackers listen to your conversations?
Via rogue apps, malicious email attachments and dodgy websites, hackers can install malware on phones that spies on everything the user does. The Android malware RedDrop, for example, can steal photos, files and information about the victim’s device, and it can listen in on their calls.
What can be seen if phone is hacked?
“Therefore, if someone hacks your phone, they would have access to the following information: email addresses and phone numbers (from your contacts list), pictures, videos, documents, and text messages.” Additionally, he warns, hackers can monitor every keystroke you type on the phone’s keyboard.
Can someone hack my phone and see what I am doing?
It masks your IP address and encrypts your traffic, thus enhancing your privacy and security. Since hackers won’t be able to identify you online and monitor what you’re doing on your smartphone, they will have fewer ways to harm you. VPN is also useful if you use public Wi-Fis, which are not always safe.