network boot means it looks for the installs from another place on the network, instead of from a CD or the hard disk on the machine.
What is network boot used for?
What is network booting? Network booting, or booting from LAN as it is also called, is a process which allows a computer to start up and load an operating system or other program directly from the network without any locally attached storage device, like a floppy, CDROM, USB stick or hard drive.
What happens during PXE boot?
PXE Boot Process The PXE boot server will send the boot files to the client through the Trivial File Transfer Protocol (TFTP). In the DHCP server, Options 66 and 67 can be configured under scope or server options. This aids in the loading and launching of the boot files for the client computer.
What is meant by PXE boot?
The Preboot Execution Environment or PXE (commonly pronounced as pixie) is a client-server environment that enables network computers to boot over the network interface card (NIC), instead of from a CD-ROM or hard disk.
Which key is pressed to boot from network?
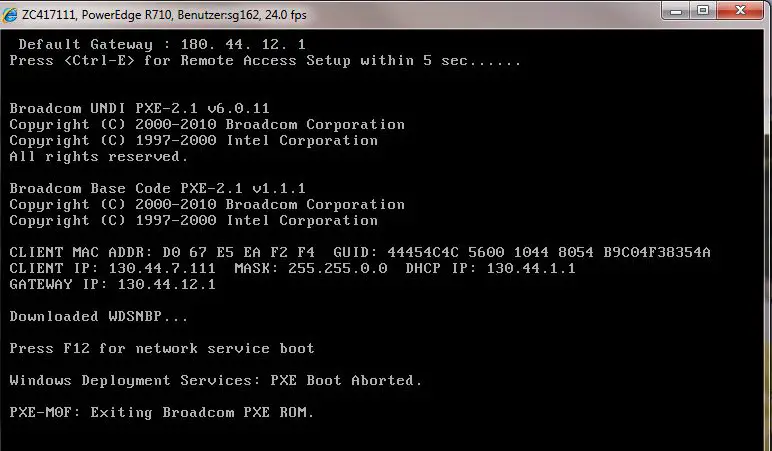
Press F12 to boot from the network.
What is network boot used for?
What is network booting? Network booting, or booting from LAN as it is also called, is a process which allows a computer to start up and load an operating system or other program directly from the network without any locally attached storage device, like a floppy, CDROM, USB stick or hard drive.
Which key is pressed to boot from network?
Press F12 to boot from the network.
What boot mode should I use?
In general, install Windows using the newer UEFI mode, as it includes more security features than the legacy BIOS mode. If you’re booting from a network that only supports BIOS, you’ll need to boot to legacy BIOS mode.
What is UEFI network boot?
Network Boot Basics When your computer powers on, the processor passes execution to a boot program that used to be known as the Basic Input/Output System (BIOS) – a system later replaced by a Unified Extensible Firmware Interface (UEFI).
What is the benefit of a PXE boot?
Some of the key advantages of PXE are: The client machine or workstation does not require a storage device or operating system. Network extension and the addition of new client computers is made easier because PXE is vendor-independent. Maintenance is simplified because most tasks are performed remotely.
What is network boot in BIOS?
Network booting, shortened netboot, is the process of booting a computer from a network rather than a local drive. This method of booting can be used by routers, diskless workstations and centrally managed computers (thin clients) such as public computers at libraries and schools.
How do I stop PXE boots?
Power on the system and Press F1 to enter UEFI setup menu. Enter Network page and disable the PXE mode from Network Boot Configuration. Restart the system.
What is a PXE boot in Windows?
PXE is an industry standard created by Intel that provides pre-boot services within the devices firmware that enables devices to download network boot programs to client computers. Configuration Manager relies on the Windows Deployment Services (WDS) server role via the WDS PXE provider.
Is PXE boot secure?
One of the key issues with PXE is a lack of security. The TFTP & UDP transactions associated with PXE may be the last unencrypted traffic on your network and are trivial to intercept. This boot process goes against the “zero trust” concept applied to today’s networks.
How do I boot my computer from a network?
Press F2 continuously when you power up your machine until it enters its BIOS Setup. Navigate to the Boot menu. Enable Boot to Network. Press F10 to save changes and exit the BIOS setup.
Should I enable boot on LAN?
If you are using only operating systems that have driver support for the Gigabit LAN controller, then you should disable the LAN Boot ROM BIOS option. This reduces the boot time (slightly) and frees up memory that would have been taken up by the boot ROM.
Should secure boot be enabled?
Secure Boot must be enabled before an operating system is installed. If an operating system was installed while Secure Boot was disabled, it will not support Secure Boot and a new installation is required.
How long does network boot take?
It can take ~45min to an hour.
What is needed for PXE boot?
To use PXE Network Boot, you need a PXE-enabled network card. Most of the on-board network cards in modern computers support PXE out of the box. But if your computer is older, you may need to get a PCI network card that supports booting from the network.
What is network boot used for?
What is network booting? Network booting, or booting from LAN as it is also called, is a process which allows a computer to start up and load an operating system or other program directly from the network without any locally attached storage device, like a floppy, CDROM, USB stick or hard drive.
Which key is pressed to boot from network?
Press F12 to boot from the network.
Which is faster UEFI or legacy?
Legacy uses the MBR partition scheme. UEFI provides faster boot time. It is slower compared to UEFI. Since UEFI uses the GPT partitioning scheme, it can support up to 9 zettabytes of storage devices.