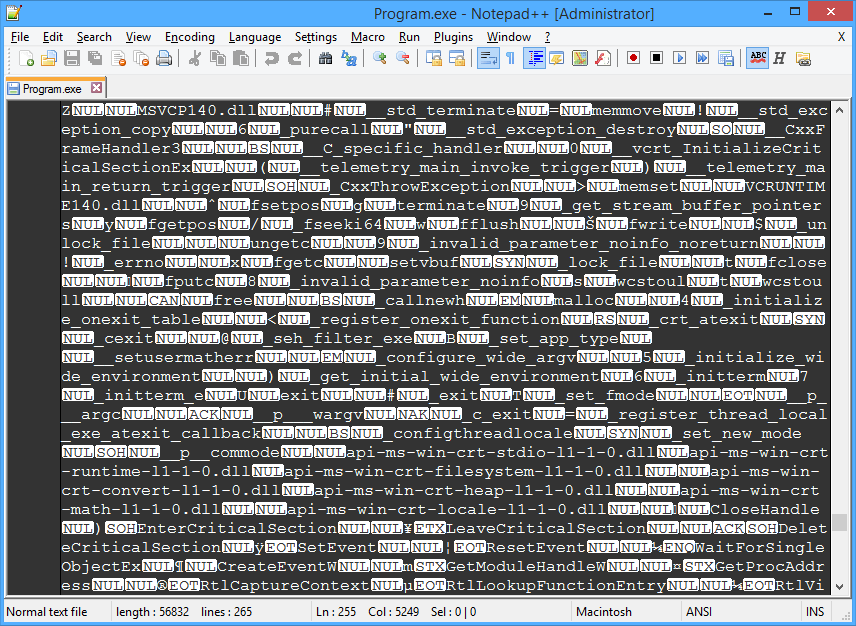
Each EXE file contains data that Windows uses to recognize, read, and run the program the file contains. This data is saved in a compiled, binary format sometimes referred to as machine code. EXE files also often contain additional program resources, such as the program’s icon and its GUI graphics assets.
How can I see what is inside an EXE file?
The exe files are self-extracting zip files. You can open them with winrar, winzip, 7z, and others, such as command line unzip that you can get on most platforms.
What is .exe horror?
EXE Games are a type of Horror Game often inspired by the infamous indie game duology Sonic. EXE. They usually involve the player character moving across the screen and seeing disturbing imagery, as they are stalked and usually killed by a corruption of a famous gaming character.
What language is .exe written in?
An EXE file is a type of program that runs in Microsoft Windows. It consists of binary, machine language code that’s not designed to be read or written by humans.
Can you read an exe file?
Until an exe runs its just a binary file, so yes you can read it.
Can I get code from exe file?
A .exe is a binary code, unless its instrumented with source code for debugging its close to impossible to get the source code.
Can exe files be hacked?
One of the most common tricks used by hackers is to get unsuspecting users to click on a malicious .exe file which leads to malware being downloaded onto a computer. They’re usually sent to you as an email attachment with the email offering some form of compelling inducement to get you to open the attachment.
Can EXE file cause cyber incident?
One of the most common tricks used by hackers is to get unsuspecting users to click on a malicious .exe file which leads to malware being downloaded onto a computer. They’re usually sent to you as an email attachment with the email offering some form of compelling inducement to get you to open the attachment.
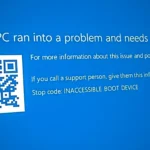
How can I tell if an EXE file has a virus?
Scan the EXE With VirusTotal Another way to find out if the EXE is legit is to scan it with VirusTotal. You simply upload the suspicious file on the VirusTotal website, and this online scanner will check it for all types of malware.
Can exe files be deleted?
As you said, since you can download them at any time, it is ok to delete EXE files.
Why does Sonic EXE call himself God?
Exe’s idolization of Sonic is what inspired Exe to look like him and even create a world that has elements related to Sonic’s world. Due to Exe’s immense powers, he views himself as a god, which he technically is since he created his world.
Is Sonic EXE a virus?
Overview. Malware Sonic, or Mal, for short, is a computer virus that was made to look like a Sonic the hedgehog fan game to fool people into downloading it. The virus later became conscious and nowadays it just likes surfing the web trying to find computers to get inside of and control.vor 6 Tagen
Is .exe copyrighted?
You’re fine with using .exe. (“File extensions are functional, and functional uses cannot be trademarked.”) Might not be the best choice, though, because of filename issues.
Can I convert exe to APK?
No, EXE files cannot run on Android, but you can convert EXE files to APL files and then run them. All the applications or programs run on Android devices are in . apk format. You cannot directly use the .exe file in your Android device, first need to convert it into .
How do I extract an EXE file without installing it?
Use WinZip In order to open an exe file without installing it, make sure to right-click on the Windows Installer files and extract their contents. By using this software you will also get access to a complex variety of features that will keep you efficient.
How do I run exe files on another computer?
You may Share a folder containing the .exe on your computer within the domain and use telnet to get a command line on the other computer to run the program.
How do I unpack an EXE file?
When you open the EXE file in 7-Zip, you’ll be shown a list of files and folders that the EXE file contains. You can double-click folders to see the files stored inside. You can select multiple files by holding Ctrl and clicking each one. Click the “Extract” button after selecting the files.
How can I tell if an exe is a virus?
Scan the EXE With VirusTotal Another way to find out if the EXE is legit is to scan it with VirusTotal. You simply upload the suspicious file on the VirusTotal website, and this online scanner will check it for all types of malware.
How do I remove the exe virus from my laptop?
Now to actually delete the virus from the system go to system32 folder and delete the regsvr.exe virus file from there (you will need to uncheck the option of “Hide Protected System Files and Folders” in Folder Options to view the virus file).
Can a PDF file contain a virus?
Can PDFs have viruses? Yes. Because PDFs are one of the most universally used file types, hackers and bad actors can find ways to use these normally harmless files — just like dot-com files, JPGs, Gmail, and Bitcoin — to create security threats via malicious code.
How can I tell if Task Manager has a virus?
If you’re curious about whether a specific program is malicious, right-click it in the Task Manager and select “Search Online” to find more information. If information about malware appears when you search the process, that’s a sign you likely have malware.
Which virus attaches itself directly to an exe?
Direct Action Virus – When a virus attaches itself directly to a .exe or .com file and enters the device while its execution is called a Direct Action Virus. If it gets installed in the memory, it keeps itself hidden. It is also known as Non-Resident Virus.