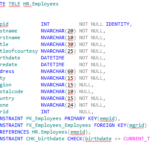
A bypass code is a temporary passcode created by an administrator for a specific user.
What is bypass in coding?
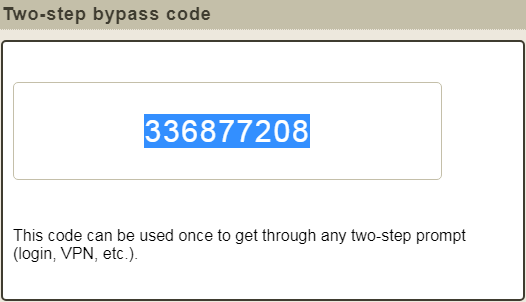
What are bypass codes? Bypass codes are nine-digit passcodes that you can use to complete multi-factor authentication prompts. Enter the codes in the Passcode field of the MFA prompt. DIT recommends you use bypass codes as a backup for when you do not have your primary MFA device available.
Why is duo asking for a bypass code?
Duo Bypass Codes can be used to access resources protected by Duo when your device is unavailable. You may also need to use Bypass codes if your device is lost, stolen, or replaced. Bypass codes should be placed in a secure location.
How do I generate a code from duo?
Use your smartphone to generate passcodes from the Duo Mobile app. To use, simply open the app and press the gray icon in the upper right-hand side of the app for iOS and Android (pointed by the red arrow in the image below) or the Generate Passcode button on Microsoft OS devices.
What is bypass in coding?
What are bypass codes? Bypass codes are nine-digit passcodes that you can use to complete multi-factor authentication prompts. Enter the codes in the Passcode field of the MFA prompt. DIT recommends you use bypass codes as a backup for when you do not have your primary MFA device available.
Can Windows password be bypassed?
Passwords can be reset or bypassed on every operating system, so even if you’ve forgotten yours, there may be a way in. This also means that evildoers can likely get into your system if they have access to it—and it’s way easier than you think.
How do you bypass a ICD 10 PCS code?
ICD-10-PCS Coding Guidelines: Bypass Procedures Bypass procedures are coded by identifying the body part bypassed “from” and the body part bypassed “to.” The fourth character body part specifies the body part bypassed from, and the qualifier specifies the body part bypassed to.
What is the root operation of bypass?
Bypass-Root Operation 1 Bypass is defined as altering the route of passage of the contents of a tubular body part. Rerouting contents of a body part can be done in three ways: To a downstream area of the normal route.
Can Duo be bypassed?
A user must have a valid Duo authentication device enrolled (like a phone or hardware token) in order to use a bypass code to authenticate. Bypass codes are not intended as a user’s only 2FA method. Bypass codes expire after being used the allowed number of times, or after an administrator-defined amount of time.
What is the manual activation code for Duo Mobile?
Click the Activate Duo Mobile link in the “Device Info” section. This link is only available when you set the phone type to “Mobile” and selected something other than “Unknown” as the platform. Then on the next page click the Generate Duo Mobile Activation Code button.
Why is my Duo code not working?
This most commonly occurs when you get a new device, reformat or restore a device, delete the Duo Mobile app, or temporarily disable an account on which you have enabled two-factor authentication. In order for passcodes to work again, you must reconnect your account(s) to the Duo Mobile app.
How long do Duo Mobile codes last?
By default, new Duo SMS passcodes are set to never expire for users authenticating to protected applications.
What is bypass authorization?
This refers to an attacker gaining access equivalent to an authenticated user without ever going through an authentication procedure. This is usually the result of the attacker using an unexpected access procedure that does not go through the proper checkpoints where authentication should occur.
What is an example of authentication bypass?
Examples of ‘Authentication Bypass Vulnerability’ SHAREit History Database. SHAREit MediaStore Database.
How authentication is bypassed by the attackers explain any two ways of authentication in Web?
Bypassing 2FA with conventional session management The attacker clicks on the ‘change password’ link. The attacker requests the password reset token. The attacker uses the password reset token. The attacker logs into the web application.
What is bypass in coding?
What are bypass codes? Bypass codes are nine-digit passcodes that you can use to complete multi-factor authentication prompts. Enter the codes in the Passcode field of the MFA prompt. DIT recommends you use bypass codes as a backup for when you do not have your primary MFA device available.
How do I enable MFA on Palo Alto firewall?
To enable 2FA/MFA for Palo Alto Networks endusers, go to 2-Factor Authentication >> 2FA Options For EndUsers. Select default Two-Factor authentication method for end users. Also, you can select particular 2FA methods, which you want to show on the end users dashboard.
How do I get into my locked Windows 10?
Press CTRL+ALT+DELETE to unlock the computer. Type the logon information for the last logged on user, and then click OK. When the Unlock Computer dialog box disappears, press CTRL+ALT+DELETE and log on normally.
What is the ICD 10 code for coronary bypass?
ICD-10-CM Code for Atherosclerosis of coronary artery bypass graft(s) without angina pectoris I25. 810.
What is the ICD 10 code for CABG?
I25. 810 – Atherosclerosis of coronary artery bypass graft(s) without angina pectoris | ICD-10-CM.
What is the ICD-10-PCS code for CABG?
What is the ICD 10 code for cardiac surgery?
ICD-10-CM Code for Intraoperative cardiac arrest during cardiac surgery I97. 710.